A sophisticated mobile phishing campaign targeting job seekers intended to install dangerous malicious software on their phones was revealed by security researchers on Tuesday.
The campaign discovered by Zimperium zLabs targets Android phones and intends to spread a variant of the Antidot banking trojan that the researchers dubbed AppLite Banker.
“The AppLite banking trojan’s ability to steal credentials from critical applications such as banking and cryptocurrency makes this scam extremely dangerous,” said Jason Soroko, a senior fellow at Sectigoa certificate lifecycle management provider in Scottsdale, Ariz.
“As mobile phishing continues to increase, it is crucial for individuals to remain vigilant about unsolicited job offers and always verify the legitimacy of links before clicking,” he told TechNewsWorld.
“The AppLite banking trojan requires permissions through the phone’s accessibility features,” added James McQuiggan, a security awareness advocate at KnowBe4a security awareness training provider in Clearwater, Fla.
“If the user is unaware,” he told TechNewsWorld, “they can allow full control of their device, making personal data, GPS location and other information available to the cybercriminals.”
‘Pig slaughter’ tactics
In a blog on Zimperium’s website, researcher Vishnu Pratapagiri explained that attackers pose as recruiters and lure unsuspecting victims with job offers. As part of their fraudulent recruitment process, he continued, the phishing campaign tricks victims into downloading a malicious application that acts as a dropper, and ultimately installing AppLite.
“The attackers behind this phishing campaign have demonstrated a remarkable level of adaptability, using diverse and sophisticated social engineering strategies to target their victims,” Pratapagiri wrote.
A key tactic used by the attackers involves masquerading as a recruiter or HR representatives from well-known organizations, he continued. Victims are tricked into responding to fraudulent emails, carefully crafted to look like authentic job offers or requests for additional information.
“People are desperate to get a job, so when they see remote work, good pay, good benefits, they text back,” said Steve Levy, chief talent advisor at DHI Groupparent company of Dice, a career marketplace for candidates seeking technology-focused roles and employers looking to hire technology talent worldwide, in Centennial, Colo.
“It starts the snowball rolling,” he told TechNewsWorld. “It’s called pig slaughter. Farmers will fatten a pig little by little, so when it’s time to cook it, they’re really big and juicy.”
After the initial communication, Pratapagiri explained that the threat actors were ordering victims to download a purported CRM Android app. Although it looks legitimate, this application functions as a malicious dropper, facilitating the deployment of the primary payload on the victim’s device.
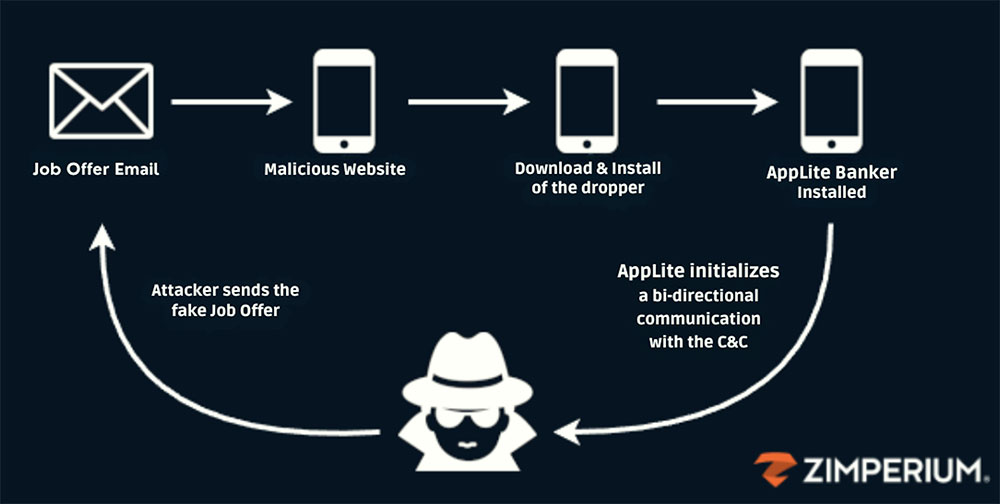
Illustration of one of the methods used to distribute and execute the AppLite malware on the victim’s mobile device. (Credit: Zimperium)
Dramatic shift to mobile attacks
Stephen Kowski, Field CTO at SlashNexta computer and network security company in Pleasanton, California, noted that the AppLite campaign represents a sophisticated evolution of techniques first seen in Operation Dream Job, a global campaign launched in 2023 by the notorious North Korean Lazarus -group management.
While the original Operation Dream Job used LinkedIn messages and malicious attachments to target job seekers in the defense and aerospace sectors, today’s attacks have expanded to exploiting mobile vulnerabilities through fraudulent job application pages and banking trojans, he explained.
“The dramatic shift to mobile-first attacks is evidenced by the fact that 82% of phishing sites now specifically target mobile devices, with 76% using HTTPS to appear legitimate,” he told TechNewsWorld.
“Threat actors have refined their social engineering tactics, moving beyond simple document-based malware to deploy sophisticated mobile banking trojans that can steal credentials and compromise personal data, demonstrating how these campaigns continue to evolve and adapt to new attack surfaces to exploit,” Kowski explains.
“Our internal data shows that users are four times more likely to click on malicious emails when using mobile devices compared to desktop,” said Mika Aalto, co-founder and CEO of Hoxhuntan enterprise security awareness solutions provider in Helsinki.
“What’s even more concerning is that mobile users tend to click on these malicious emails at an even greater rate during the late night hours or very early in the morning, suggesting that people are more vulnerable to attacks on mobile devices when their defenses are down,” he told TechNewsWorld. “Attackers are clearly aware of this and are constantly evolving their tactics to exploit these vulnerabilities.”
This new wave of cyber scams underscores the evolving tactics used by cybercriminals to exploit job seekers motivated to make a prospective employer happy, Soroko observed.
“By capitalizing on individuals’ trust in legitimate-looking job offers, attackers can infect mobile devices with sophisticated malware that targets financial data,” he said. “The use of Android devices, in particular, highlights the growing trend of mobile-specific phishing campaigns.”
“Be careful what you load onto an Android device,” he warned.
Businesses also need protection
DHI’s Levy noted that attacks on job seekers are not limited to cell phones. “I don’t think it’s just being moved to mobile phones,” he said. “We see it on all the social platforms. We see it on LinkedIn, Facebook, TikTok and Instagram.”
“Not only are these scams common, they are very insidious,” he declared. “They prey on the emotional situation of job seekers.”
“I probably get three to four of these text inquiries a week,” he continued. “They all automatically go into my junk folder. These are the new versions of the Nigerian prince emails asking you to send them $1,000 and they’ll give you back $10 million.”
In addition to its ability to mimic enterprise applications, AppLite can also impersonate Chrome and TikTok apps, demonstrating a wide range of targeting vectors, including full device takeover and app access.
“The level of access provided (to) the attackers could also include corporate credentials, applications and data if the device was used by the user for remote work or access for their existing employer,” Pratapagiri wrote.
“As mobile devices have become essential to business operations, securing them is essential, especially to protect against the wide variety of different types of phishing attacks, including these sophisticated self-targeting phishing attempts,” said Patrick Tiquet, vice president of security and architecture. . of Custodian Securitya password management and online storage company, in Chicago.
“Organizations must implement robust mobile device management policies to ensure that both corporate-issued and BYOD devices meet security standards,” he told TechNewsWorld. “Regular updates to both devices and security software will ensure that vulnerabilities are patched promptly, and protect against known threats that target mobile users.”
Aalto also recommended the adoption of human risk management (HRM) platforms to tackle the growing sophistication of mobile phishing attacks.
“When a new attack is reported by an employee, the HRM platform learns to automatically find future similar attacks,” he said. “By integrating HRM, organizations can create a more resilient security culture where users become active defenders against mobile phishing and fatigue attacks.”
+++++++++++++++++++
Ready to Sell
AISKILLSOURCE.COM