Akamai’s ransomware report released at Black Hat 2023 revealed that exploiting zero-day and one-day vulnerabilities led to a 143% increase in total ransomware victims with data exfiltration from files at the end of the death chain, now the primary source of extortion.
Jump to:
LockBit in the lead, CL0P in 2nd
The report, Ransomware on the movelooked at how exploit techniques are evolving — including attackers’ sharper focus on zero-day vulnerabilities. It showed how victims of multiple ransomware attacks were more than six times more likely to experience the second attack within three months of the first attack.
The authors of Akamai’s Security Intelligence Group reviewed data from the fourth quarter of 2021 to the second quarter of 2023. The authors reported that LockBit ensnared approximately 39% of all victim organizations tracked by Akamai, which said LockBit’s victim count was three times that of its closest competitor, the CL0P group. Number three in volume of victims, ALPHV, aka Black Cat, focused its efforts on developing and exploiting zero-day access points (Figure A).
Figure A
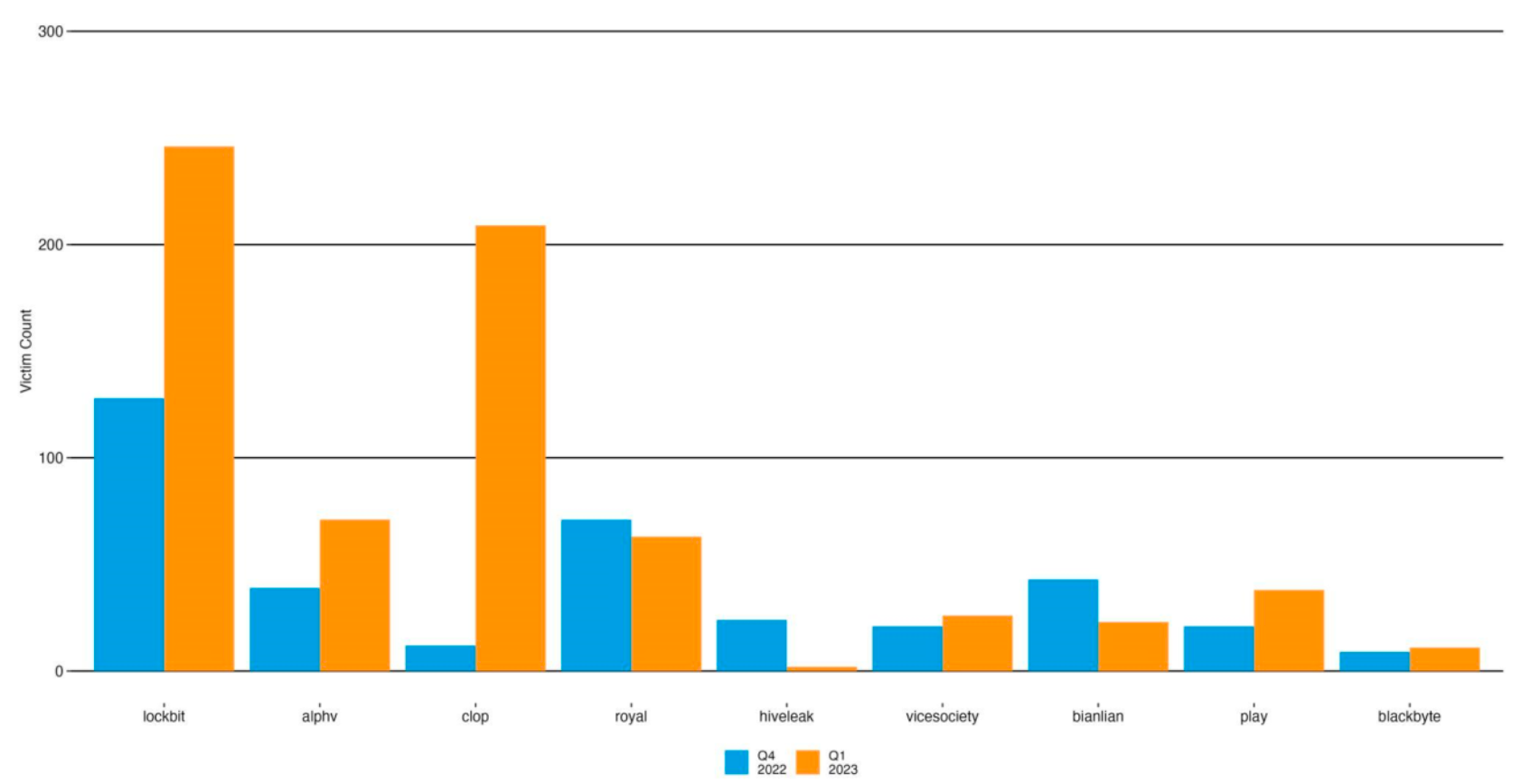
- Top ransomware groups by victim count. Image: Akamai
Anthony Lauro, director of security technology and strategy at Akamai, explained that LockBit is looking for high-value targets with zero-day vulnerabilities that companies can’t fix quickly. They tend to target and retarget these organizations and the sectors – such as manufacturing and technology, for example – where security operations generally lag. Also, he explained, malware authors can choose tools and services from a growing dark ecosystem.
Two distinct trends show how threats are evolving
The report highlighted two trends that speak to how large groups – with the scale and breadth of products, including RaaS – have stable growth and smaller groups focus on opportunities as they arise:
- The first is exemplified by LockBit, characterized by a steady count of 50 victims per month, and activity seems to be linked to its number of affiliates and its resources.
- The second, typified by groups like CL0P, includes spikes in activity exploiting critical zero-day vulnerabilities as they occur, and highly targeted security flaws.
“Malware writers can now segregate operations, which is a change,” Lauro said. “It used to be that the attackers were a single entity or group that would be responsible for malware payload delivery, exploitation and follow-up.” He added that due to the open nature of the malware market, groups like LockBit and Cl0P were able to co-opt others to carry out various tasks in the supply kill chain.
ALPHV: Rust never sleeps
Lauro said that within the tactics more often found in the second trend group, “Are the tried and true methodologies, such as Windows system vulnerabilities that are not necessarily high, because these systems are usually not available to outside queries. Attackers can still get access to it. So there are two main trends: spreading the victim base across easy targets and tactics and those using CVE and zero days looking at big players as targets.”
ALPHV, for example, second on Akamai’s list of attackers in terms of victim volume, uses the Rust programming language to infect both Windows and Linux systems. Akamai said the group exploited vulnerabilities in Microsoft Exchange server to infiltrate targets.
According to Akamai, the group spoofed a victim’s website last year (using a tick-rated domain). The new extortion technique included publishing the stolen files and leaking them on their website to tighten the thumb screws on victims and encourage the payment of ransoms.
Mid-sized organizations are the ‘Goldilocks zone’ for threat actors
In Akamai’s study, 65% of targeted organizations reported revenues of up to $50 million dollars, while those valued at $500 million dollars and more accounted for 12% of total victims, according to Akamai. They also reported that the ransomware data used was collected from the leak sites of around 90 different ransomware groups.
Let’s call it ‘Cyberfracking’
If you invested in a natural gas mining operation, you might “accidentally intentionally” reach out laterally to assets under other people’s lawns once you took out the target. LockBit attackers also reach out to victims’ customers, inform them of the incident, and use triple blackmail tactics including Distributed Denial of Service attacks.
Lauro said different stages of exploitation and delivery and execution are the first two steps. Defense is based on edge defense elements like visibility, but the rest of it is going after, moving sideways and tricking systems, or making requests that look like a “friendly” – all within the network.
SEE: Check your APIs! Akamai says observability tools sorely lacking (TechRepublic)
“Once you’re inside, most organizations are wide open, because like back then, I don’t have to download an attacker special toolsets; I can use installed tools. So there is a lack of good localized network security. We are finding more and more environments in bad shape in terms of internal visibility and over time,” he said.
CL0P for a day… a zero day
CL0P, which ranks third in terms of its number of victims over the course of Akamai’s observation period, tends to exploit zero-day vulnerabilities in managed file transfer platforms. Akamai said the group exploited a legacy file transfer protocol that has been officially deprecated since 2021, as well as a zero-day CVE in MOVEit Transfer to steal data from multiple organizations.
“It is notable how CL0P has a relatively low victim count until its activity spikes when a new zero-day vulnerability is exploited as part of its operation,” the authors of the Akamai report said. “And unlike LockBit, which has some semblance of consistency or pattern, CL0P’s attacks seem to be tied to the next big zero-day vulnerability, which is hard to predict (Figure B).”
Figure B
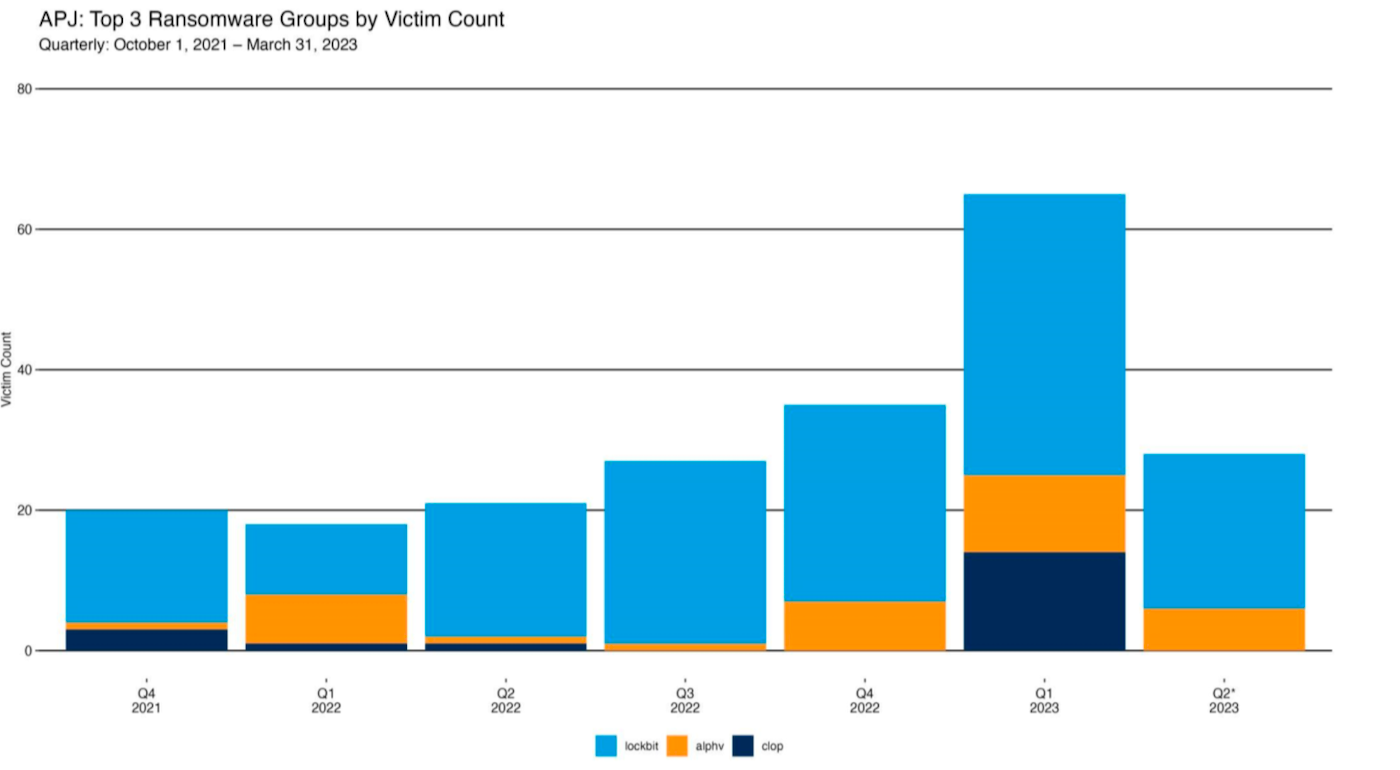
- A comparison of quarterly victims ranks among the top three ransomware groups: LockBit, ALPHV and CL0P. Image: Akamai
LockBit: a key solution
Akamai noted that LockBit, whose website looks like a legitimate web problem, is touting new tools and even a bug bounty program in its latest 3.0 version. Just like white hats, the group invites security researchers and hackers to submit bug reports in their software for rewards of up to $1 million.
Akamai noted that while the bug bounty program is primarily defensive, “It is unclear whether it will also be used to obtain vulnerabilities and new avenues for LockBit to exploit victims.” (Figure C).
Figure C
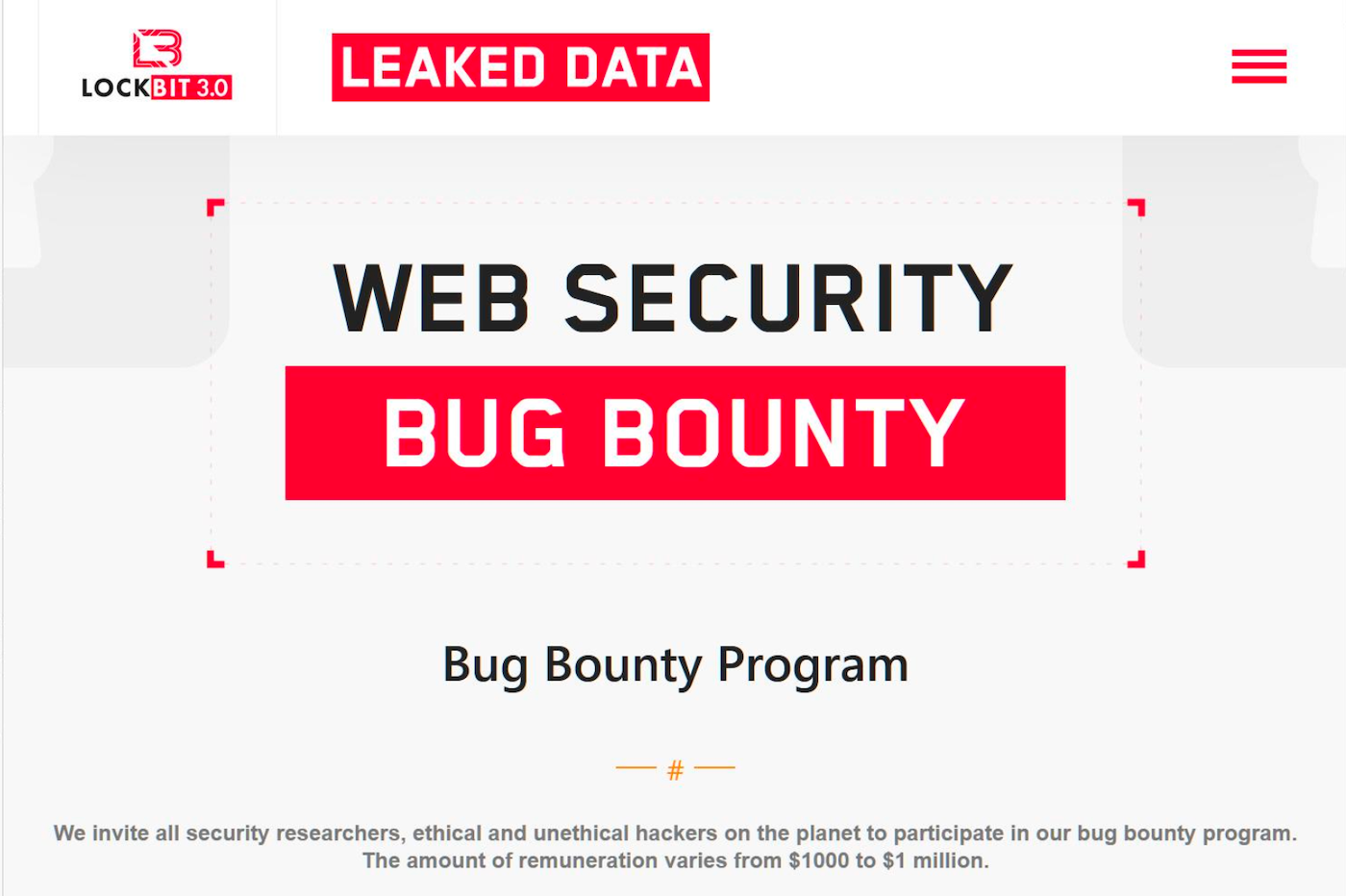
- LockBit is looking for ethical and unethical hackers. Source: Akamai via Bleeping Computer.
On its website, LockBit is looking for ethical AND unethical hackers. Source: Akamai via Bleeping Computer.
Manufacturing, healthcare in hot seat
Of all industry verticals, manufacturing saw a 42% increase in total casualties during the period Akamai surveyed. LockBit was behind 41% of the overall manufacturing attacks.
The healthcare vertical saw a 39% increase in victims during the same period, and was primarily targeted by the ALPHV (aka BlackCat) and LockBit ransomware groups.
SEE: Akamai focused on fake websites in research released at RSA
Mitigation is the best defense
Akamai’s recommendations on reducing the chance of attack and mitigating the consequences of an intrusion include adopting a multi-layered approach to cyber security that includes:
- Network mapping to identify and isolate critical systems and restrict network access in and out to put up fences in the face of threat actors’ attempts at lateral movement.
- Patch, patch, patch: update software, firmware and operating systems.
- Story shots: maintain regular offline backups of critical data and set up an effective disaster recovery plan.
- Develop and regularly test an incident response plan that outlines the steps to be taken in the event of a ransomware attack. This plan should include clear communication channels, roles and responsibilities, and a process for engaging law enforcement and cybersecurity experts.
- Train, and retrain: Don’t give employees, vendors, and suppliers access to organizational sites or systems before they’ve had (regular) cybersecurity awareness training about phishing attacks, social engineering, and other ransomware vectors.
- If you see something, say something: Encourage employees and stakeholders to report suspicious activity.
Defense is the best offense
Defensive tactics, according to Akamai, should include:
Blocking of exfiltration domains
Limit access to services that can be abused for data exfiltration by either using solutions that block known malicious url and DNS traffic, or by using solutions or controls that block access to specific domains.
Hang up those honey covered fly strips
Honey pots: use them. Akamai said they can help catch attackers and lure them to servers where their activities can be monitored
Scan and scan again
Use an intrusion detection system to conduct suspicious network scans. Akamai noted that attackers use identifying tools to finger targets within an organization’s network. You can track them down.
Check passports at the gate
Akamai suggests using outbound Internet traffic inspection tools to block known malware C2 servers. “Solutions must be able to monitor your entire DNS communications in real time and block communications to malicious domains, to prevent the malware from running properly and achieving its goals,” the firm said.
+++++++++++++++++++
TechNewsUpdates
beewire.org